- C Program To Implement Dictionary Using Hashing Passwords In Computer
- C Program To Implement Dictionary Using Hashing Passwords In Word

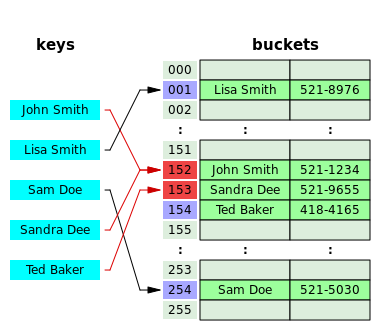
An often overlooked and misunderstood concept in application development is the one involving secure hashing of passwords. We have evolved from plain text password storage, to hashing a password, to appending salts and now even this is not considered adequate anymore. In this post I will discuss what hashing is, what salts and peppers are and which algorithms are to be used and which are to be avoided.HashingHashing is a type of algorithm which takes any size of data and turns it into a fixed-length of data. This is often used to ease the retrieval of data as you can shorten large amounts of data to a shorter string (which is easier to compare). For instance let’s say you have a DNA sample of a person, this wouldconsist of a large amount of data (about 2.2 – 3.5 MB), and you would like to find out to who this DNA sample belongs to.
C Program To Implement Dictionary Using Hashing Passwords In Computer
You could take all samples and compare 2.2 MB of data to all DNA samples in the database, but comparing 2.2 MB against 2.2 MB of data cant take quite a while, especially when you need to traverse thousands of samples. This is where hashing can come in handy, instead of comparing the data, you calculate the hash of this data (in reality, several hashes will be calculated for the different locations on the chromosomes, but for the sake of the example let’s assume it’s one hash), which will return a fixed length value of, for instance, 128 bits. It will be easier and faster to query a database for 128-bits than for 2.2 MB of data.The main difference between hashing and encryption is that a hash is not reversible. The suitability of a hash-function depends on how fast the function is in software compared to how expensive it is to implement in hardware. Both SHA-2 and SHA-3 are relatively cheap in hardware, but SHA-3 is probably even a bit more hardware friendly.The quality of your software implementation is pretty important for this ratio as well. For example.net’s implementation( Rfc2898DeriveBytes) is horribly slow compared to a good implementation.
We provide the direct link as well as Nokia store’s official link for Nokia Asha Whatsapp as below. Download whatsapp for nokia asha 203 images.
C Program To Implement Dictionary Using Hashing Passwords In Word
With a good implementation you can choose a higher iteration count (and thus higher security) at the same performance cost.